Lately, it might seem like everyone, from big companies to your casual acquaintances, is talking about data and data security. Sentences such as, “They’re collecting and selling your data!” or “Did you see the news that XYZ got breached?” are likely something that you hear on a regular basis.
Technology is advancing at a rapid speed, and we have become more data-reliant than ever. This, naturally, means that data, and everything that comes with it isn’t just an IT sector concern anymore. Data is intertwined in all of our lives, whether we’re fully aware of it or not.
The amount of data generated by people through their digital interactions continues to grow on a daily basis. According to an estimate of DOMO, a single person generates 1.7 MB per second; just from regular everyday activities like checking the news in the morning, listening to a podcast on the way to work, scrolling through social media at work, and using GPS navigation. All of these actions involve exchanging, tracking, and storing data.
With the increasing amount of personal and sensitive information being stored and shared online, the need for robust data security measures has never been greater. From financial institutions and healthcare providers to small businesses and individuals, the protection of sensitive information is a top priority.
However, as technology continues to evolve and cyber threats become more sophisticated, it is becoming increasingly more challenging to keep up with the latest data security trends and best practices.
Here, we are going to explore the current state of data security and database management and provide insight into how individuals or organizations can stay vigilant in the face of rising cybercrime, as well as whether or not these database management and data security can exist in cohesion.
The Fundamentals of Data Security and Database Management
As we’ve already established, data is the lifeblood of any organization, across various industries. It’s critical to protect data from all unauthorized access and security threats. However, to fully grasp the importance of this issue, it’s crucial to understand what database management and data security actually mean.
Database Management
The history of database management dates back to the 1960s when the first database management systems were developed to manage large amounts of data. Since then, database management has evolved significantly, with the development of relational database management systems and the widespread adoption of technology such as cloud computing and big data analytics.
With the rise of data reliance, database management systems are more important than ever. For those who are unsure of what database management systems provide a standardized and automated way to store, retrieve, and manipulate data, and support various operations such as data backup and recovery, data security, and data integration. Without a database management system, these tasks would have to be performed manually, which could be time-consuming, error-prone, and lacking in scalability.
Organizations generate and store massive amounts of data and rely on it to drive business decisions. Effective database management is critical to ensure the accuracy, reliability, and availability of data, and to protect sensitive information from threats such as cyber-attacks, data breaches, and data loss.
Data Security
Data security, on the other hand, is the set of practices and protocols that are put in place to protect data from unauthorized access, modification, or disclosure. The evolution of data security has paralleled advancements in computing and technology. The requirement for data security emerged as computer usage became widespread in the business and government sectors during the 1960s and 1970s.
As the prevalence of computer systems grew and the quantity of sensitive data stored on them expanded, it became apparent that measures must be implemented to secure this data from unauthorized access and the risk of breaches.
Database management and data security are closely related as database management play a crucial role in maintaining data security and data security is essential in ensuring the integrity and availability of data. Together, they form a comprehensive approach to data protection.
While database management and data security may seem unrelated, they actually coexist and work together to protect the data stored on a website or application. Proper database management helps to ensure that sensitive information is stored securely and that backups are available in case of data loss. Additionally, a website or application that is well-secured is less likely to be targeted by hackers, as it is likely to have fewer vulnerabilities.
Data security, on the other hand, is the process of protecting the website or application and its associated databases from unauthorized access or breaches. This includes measures such as encryption, secure authentication, and regular backups. Data security is essential for protecting sensitive information such as personal data and financial information from cyber-attacks and data breaches. It also ensures that data ownership remains with the rightful owner and is not accessible to unauthorized parties.
Data security and data ownership are becoming increasingly important as technology advances and more industries become reliant on data. Database management and data security are two critical aspects of maintaining a website, application, or running a company. Properly managing both can help ensure that a website or application is secure and that its data is protected, and that data ownership remains with the rightful owner.
Poor Database Management & Poor Data Security: The Consequences
Poor database management and poor data security can have severe consequences for organizations. Inadequate data management can result in data loss, corruption, or duplication, causing operational disruptions and reducing productivity. Furthermore, weak data security can lead to data breaches, resulting in the theft or loss of sensitive information such as personal data, financial information, and confidential business information.
This can result in significant reputational damage, loss of trust from customers and partners, legal liabilities, and financial losses. In extreme cases, poor data management and security can even result in the closure of a business.
The 2021 Thales Cloud Security Study reveals a concerning trend: despite a rise in cyberattacks aimed at data in the cloud, a large majority of American businesses (83%) are not encrypting at least half of the sensitive data they store in the cloud. This is particularly worrying as a significant portion of organizations (24%) have reported that a majority of their data and workloads are now in the cloud, making them a prime target for cybercriminals.
Vormetric Data Threat Report stated that 85% of enterprises store sensitive data in the cloud. Storing sensitive data on cloud services may seem like an easy and convenient solution for businesses and enterprises due to its accessibility, scalability, and cost-effectiveness, but it also brings some risks and challenges that are worth considering.
For starters, cloud services can easily be a target for hacking or data breaches, which could lead to sensitive data getting into the wrong hands. On top of that, businesses might not have full control over who has access to their data or how it's being used if it's stored on a cloud service. And let's not forget about compliance issues - some businesses have restrictions on what types of data they can store on cloud services.
If the cloud service provider has a technical glitch, the business might not be able to access your sensitive data, leaving the company and end-users in a tough spot.
How Can Database Security Be Achieved
Database security is a complex issue, despite the fact that it’s a crucial aspect of modern computing. Keeping sensitive data secure requires constant vigilance and a commitment to best practices. This, however, is often easier said than done.
Database security can be achieved through a combination of technical and administrative measures. Technical measures include using encryption to secure sensitive data, implementing firewalls to prevent unauthorized access, regularly updating software to address vulnerabilities, and implementing backup and recovery strategies to ensure data availability.
Administrative measures include developing and enforcing access control policies, conducting regular security audits and monitoring, providing regular security training to employees, and implementing an incident response plan in case of security breaches.
To ensure effective database security, it is important for organizations to adopt a multi-layered approach, combining technical and administrative measures to provide a comprehensive security framework for their databases.
However, these solutions operate with a centralized infrastructure. A centralized infrastructure means that they are susceptible to certain limitations, such as limited scalability, high latency, single point of failure, and more prone to data breaches. This means that you can implement all the aforementioned safety practices, and still suffer a data leak.
The New Decentralized Solution
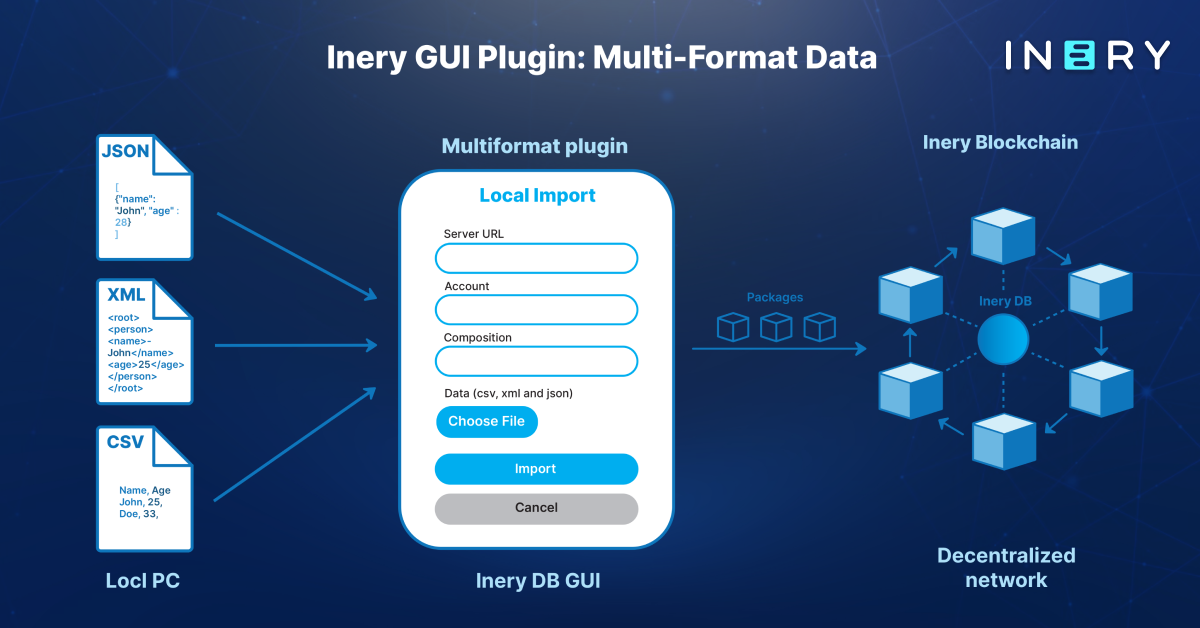
Inery introduces a new decentralized solution for database management that aims to bridge the gap between database management and data security, in a fast and cost-effective way. Inery’s decentralized database management system utilizes the revolutionary power of blockchain technology to provide secure, transparent, and decentralized storage of all data – especially critical or sensitive data.
The users of Inery are the only ones to have access to their access keys, meaning that data can’t be changed or deleted by third parties. In other words, you are the one who has full power over your data. User data is managed via multiple servers across the network — also known as MEM nodes. This ensures high speed, low cost, and accelerates data recovery speed.
All transactions within Inery’s blockchain are validated by the Proof of Equal Stake consensus mechanism, guaranteeing that each transaction is true and correct. Running on POS assures top-notch security. Inery is Sybil attack resistant, and more sustainable with high throughput, thanks to this consensus mechanism.
With Inery’s solution, there is no single point of failure, and data can be managed in a secure and decentralized manner, making it impenetrable to cyber-attacks and data leaks. The system offers improved data privacy, accessibility, and reliability compared to traditional centralized database systems.
All of this makes Inery particularly suitable for organizations handling sensitive information, such as financial institutions, healthcare providers, and governments.
Final Words
Database management and data security are two critical aspects of maintaining a website, application, or business altogether; whether it’s the personal data of users or sensitive data important to the company.
With Inery, you can have the best of both worlds: seamless database management and unbeatable data security. Our decentralized solution will revolutionize the way organizations in various industries manage their databases and ensure the safety and security of their valuable data.
Take a quantum data leap with Inery, and experience the pure power of decentralization in a sustainable, highly secure, and cost-effective way.

Inery•
1 year ago
Cutting Inefficiencies in ERP Systems With Inery
Enterprise Resource Planning has a lot to gain from implementing Inery’s blockchain technology. Find out what by clicking here. ...READ MORE
-1689860359.png)
Share

Inery•
6 months ago
The World Wide Web Made For Users - By Users
Discover a digital revolution with Inery's Web3 vision, empowering users to redefine their online experiences through blockchain, decentralization, and user-controlled data assets. ...READ MORE

Share

Inery•
2 years ago
Our Vision for Blockchain: Doing what has never been done before
A frontier for other blockchains while offering a foundation for applications, systems and even layer-1 blockchains. ...READ MORE

Share

Inery•
4 months ago
The IneryDB Glossary
For an easier time making heads or tails of IneryDB, skim through this handy glossary of key IneryDB terms. ...READ MORE

Share
Most popular today

-1675941002.png)